In today’s digital landscape, where cybersecurity plays a vital role, understanding the significance of MAC addresses and their manipulation is essential. A Media Access Control (MAC) address is a unique identifier assigned to network interfaces for communication on a local network. It serves as a means to identify devices on a network, making it a prime target for security measures like MAC filtering. This blog post will delve into the intriguing world of MAC addresses, exploring how to change them without the use of tools and bypass MAC filtering, all from the perspective of a real hacker.
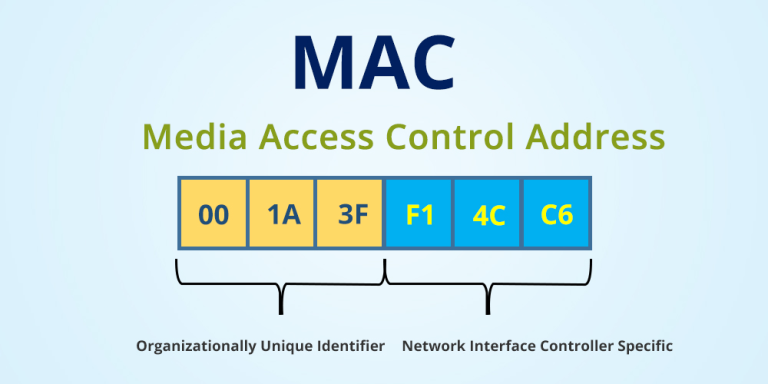
- Understanding MAC Addresses: Before diving into changing MAC addresses, it is crucial to grasp their basic structure and significance. A MAC address is a 48-bit identifier expressed as six pairs of hexadecimal digits (e.g., 01:23:45:67:89:ab). The first three pairs usually represent the manufacturer’s unique identifier, while the remaining three pairs are the device’s serial number.
- Reasons for Changing MAC Addresses: There are legitimate reasons for changing a MAC address, such as network troubleshooting or privacy concerns. However, it is essential to emphasize that using this knowledge for illegal activities is unethical and against the law.
- Changing MAC Addresses without Tools: Traditionally, changing MAC addresses required specialized software or tools. However, a real hacker knows how to manipulate MAC addresses without relying on external tools. Here’s how:a. Windows Operating System:
- Open the Device Manager by right-clicking on the “Start” menu and selecting “Device Manager.”
- Expand the “Network Adapters” section and locate the network adapter you want to change the MAC address for.
- Right-click on the network adapter and select “Properties.”
- In the “Properties” window, navigate to the “Advanced” tab.
- Locate and select the “Network Address” or “Locally Administered Address” option.
- Enable the option and enter the new MAC address, ensuring it follows the correct format (e.g., 01:23:45:67:89:ab).
- Click “OK” to save the changes.
- Open the “System Preferences” by clicking on the Apple logo in the menu bar and selecting “System Preferences.”
- Click on “Network” and select the network connection you want to modify.
- Click on the “Advanced” button in the lower right corner.
- In the “Hardware” tab, locate the “MAC Address” field and enter the new MAC address, following the correct format.
- Click “OK” to save the changes.
- Open a terminal window.
- Use the “ifconfig” or “ip” command to identify the network interface you want to modify.
- Use the “ifconfig [interface] down” command to deactivate the interface.
- Use the “ifconfig [interface] hw ether [new MAC address]” command to assign the new MAC address.
- Use the “ifconfig [interface] up” command to reactivate the interface.
- Bypassing MAC Filtering: MAC filtering is a security measure employed by network administrators to only allow specific MAC addresses to access a network. However, a skilled hacker can bypass this restriction. Here are a few techniques:a. MAC Spoofing: MAC spoofing involves changing your device’s MAC address to match an allowed MAC address on the network. By impersonating an authorized device, you can bypass MAC filtering. Refer back to the steps mentioned earlier for changing MAC addresses without tools.b. ARP Spoofing: Address Resolution Protocol (ARP) spoofing is a technique where an attacker sends false ARP messages to redirect network traffic through their device. By manipulating the ARP table, an attacker can trick the network into thinking their device has a legitimate MAC address, allowing them to bypass MAC filtering.c. Wireless MAC Filtering Workarounds: If MAC filtering is applied to a wireless network, a hacker can bypass it through various methods:
- MAC address cloning: Identifying an allowed MAC address on the network and cloning it on the attacker’s device.
- Wireless packet injection: Utilizing tools like AirCrack-ng to inject specially crafted packets into the wireless network, creating a loophole to bypass MAC filtering.
Conclusion: Changing MAC addresses and bypassing MAC filtering can be useful for legitimate purposes like troubleshooting or privacy concerns. However, it is essential to understand that using these techniques for illegal activities is unethical and illegal. The knowledge shared in this blog post aims to raise awareness and enhance cybersecurity understanding. By gaining insight into these techniques, both network administrators and users can take appropriate measures to safeguard their networks and data from potential threats.