The rise of malware attacks in recent years has made it increasingly important for cybersecurity professionals to have the ability to reverse engineer malware. Reverse engineering is the process of deconstructing a program or code to understand how it functions and identify any vulnerabilities or malicious components that may be hidden within it. In this blog, we’ll take a closer look at how reverse engineering can be used to handle malware effectively.
Why is Reverse Engineering Important for Malware Handling?
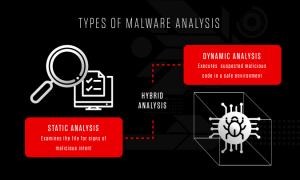
Malware is a term used to describe malicious software that is designed to harm computer systems and networks. It can be delivered through email, websites, downloads, or other methods, and can cause significant damage to organizations, including financial loss, data theft, and reputational damage.
Reverse engineering can be a powerful tool for handling malware because it enables cybersecurity professionals to understand how it works, how it was designed, and how it can be neutralized. By breaking down the code, they can identify any vulnerabilities or malicious components that may be hidden within it and develop strategies to prevent or mitigate attacks.
Steps Involved in Reverse Engineering Malware
Reverse engineering malware involves several steps, including the following:
- Obtaining the malware: Malware can be obtained from a variety of sources, including honeypots, malware repositories, and through incident response efforts.
- Disassembling the code: Once the malware has been obtained, the next step is to disassemble the code using a disassembler tool. This allows the code to be read in a human-readable format, making it easier to identify any malicious components.
- Analyzing the code: With the code disassembled, the next step is to analyze it to identify any malicious components, including backdoors, trojans, or other types of malware.
- Developing a strategy: Once the malicious components have been identified, cybersecurity professionals can develop a strategy to prevent or mitigate future attacks. This may involve patching vulnerabilities, blocking IP addresses, or other measures.
- Reversing the code: In some cases, cybersecurity professionals may need to reverse the code to identify the source of the attack. This can be a complex process, but it can be critical for identifying the individual or organization responsible for the attack.
Benefits of Reverse Engineering Malware
Reverse engineering malware offers several benefits, including the following:
- Improved threat intelligence: By reverse engineering malware, cybersecurity professionals can gain a deeper understanding of how attackers operate, including their tactics, techniques, and procedures.
- Better incident response: With a deeper understanding of how malware works, cybersecurity professionals can respond more effectively to incidents, including containing the damage and preventing further attacks.
- More effective prevention strategies: By identifying vulnerabilities and malicious components in malware, cybersecurity professionals can develop more effective prevention strategies to protect against future attacks.
Conclusion
Reverse engineering is a critical tool for handling malware effectively. By disassembling, analyzing, and reversing the code, cybersecurity professionals can gain a deeper understanding of how malware works and develop more effective prevention and response strategies. As the threat of malware continues to grow, the importance of reverse engineering in cybersecurity will only continue to increase.
Reverse engineering is a technique that is commonly used in cybersecurity to identify and neutralize malicious code. It involves breaking down the code of a program or application to understand how it works and identify any vulnerabilities or malicious components that may be hidden within it.
In the case of malware handling, reverse engineering can be particularly useful because it allows cybersecurity professionals to gain a deeper understanding of how the malware operates. By analyzing the code, they can identify the specific functions that the malware performs, including how it spreads, how it communicates with its command and control servers, and how it executes its payload.
Reverse engineering can also help cybersecurity professionals identify any weaknesses or vulnerabilities in the malware that can be exploited to neutralize or prevent it from causing harm. For example, they may be able to identify specific functions or commands that can be disabled or blocked to prevent the malware from executing its payload.
In addition to helping cybersecurity professionals respond to incidents and prevent future attacks, reverse engineering can also provide valuable insights into the tactics, techniques, and procedures used by attackers. By analyzing the code of malware, cybersecurity professionals can gain a deeper understanding of how attackers operate and develop more effective strategies for detecting and preventing future attacks.
Overall, reverse engineering is a critical tool for handling malware in cybersecurity. It allows cybersecurity professionals to gain a deeper understanding of how malware works and develop more effective strategies for responding to incidents, preventing future attacks, and protecting critical systems and data.