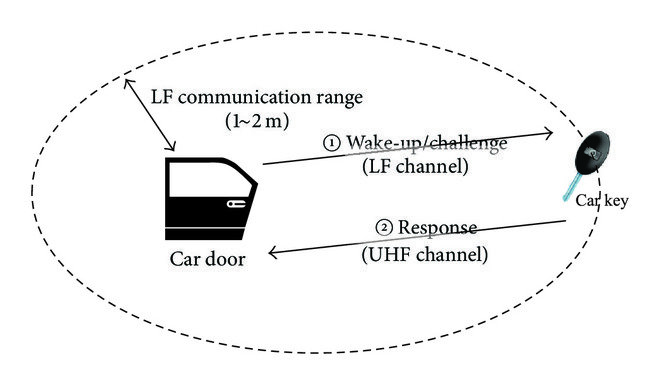
PKES is a cryptographic system that uses two keys – a public key and a private key – to encrypt and decrypt data. It is widely used for secure communication over the internet, including online transactions, email communication, and messaging. The strength of a PKES system lies in the mathematical complexity of the algorithms used to generate the keys.
Attacking a PKES system can have severe consequences, both for the attacker and the victim. First of all, it is illegal and can result in criminal charges and imprisonment. Second, if successful, the attacker can access sensitive information such as credit card numbers, social security numbers, and other personal data. This information can be used for identity theft, financial fraud, and other malicious activities.
There are several ways to attack a PKES system, including brute-force attacks, man-in-the-middle attacks, and side-channel attacks. Brute-force attacks involve trying every possible combination of keys until the right one is found. Man-in-the-middle attacks intercept and alter communication between two parties, allowing the attacker to access the private key. Side-channel attacks exploit weaknesses in the hardware or software used to generate the keys.
Fortunately, PKES systems are designed to be resilient against attacks. They use algorithms that are mathematically complex and practically impossible to crack with current computing power. Additionally, PKES systems are constantly updated to address any known vulnerabilities.
In conclusion, attacking a PKES system is illegal and unethical. It can have severe consequences for the attacker and the victim. Instead of resorting to illegal activities, it is recommended to use legal and ethical means to address any concerns or issues with a PKES system. This can include reporting vulnerabilities to the system administrators or using legal channels to seek redress.
Public Key Encryption System (PKES) is a type of encryption that uses two keys, a public key, and a private key. The public key is used for encrypting the data, while the private key is used for decrypting the data. This means that anyone can encrypt the data using the public key, but only the person with the private key can decrypt the data. This makes PKES systems highly secure and widely used in various applications such as online transactions, email communication, messaging, and more.
However, despite their strong security features, PKES systems can still be vulnerable to attacks. The most common types of attacks against PKES systems include brute force attacks, man-in-the-middle attacks, and side-channel attacks.
Brute force attacks involve trying every possible combination of keys until the correct one is found. This is an incredibly time-consuming process as the number of possible key combinations is enormous. Therefore, PKES systems typically use keys that are large enough to make brute force attacks impractical.
Man-in-the-middle attacks involve intercepting and altering the communication between two parties, allowing the attacker to access the private key. This can be done by redirecting the communication through a fake server or by using other tactics such as session hijacking. PKES systems are designed to prevent such attacks by using secure communication protocols, digital signatures, and other security measures.
Side-channel attacks exploit vulnerabilities in the hardware or software used to generate the keys. These attacks can be highly sophisticated and can take advantage of things like power consumption, electromagnetic radiation, or other physical characteristics of the system. PKES systems are designed to prevent such attacks by using hardware and software that is resistant to side-channel attacks.
The consequences of attacking a PKES system can be severe. As mentioned earlier, it is illegal and can result in criminal charges and imprisonment. Additionally, if successful, the attacker can access sensitive information such as credit card numbers, social security numbers, and other personal data. This information can be used for identity theft, financial fraud, and other malicious activities.
In summary, PKES systems are highly secure and widely used in various applications. However, they can still be vulnerable to attacks, and it is important to use legal and ethical means to address any concerns or issues with a PKES system. Attacks against PKES systems are illegal and can result in severe consequences for the attacker and the victim. It is always best to follow legal and ethical practices to ensure the security and privacy of all parties involved.
Advantages:
- High Security: PKES is highly secure due to its use of two keys, one public key, and one private key. This makes it extremely difficult for anyone to intercept, decrypt or tamper with the data being transmitted.
- Easy to use: PKES is relatively easy to use compared to other encryption methods. It eliminates the need for secure key exchange, which can be complicated in other encryption methods.
- Widely used: PKES is widely used in various applications such as online transactions, email communication, messaging, and more. This is because of its high level of security and ease of use.
- Digital Signatures: PKES provides a mechanism for digital signatures, which enables the receiver to verify the authenticity of the sender.
- Scalability: PKES can be used for securing communication between two parties, or it can be used to secure communication between multiple parties in a network.
Disadvantages:
- Computational Complexity: PKES encryption and decryption require a significant amount of computational power. This can make it difficult to use in certain applications where computational resources are limited.
- Key Management: PKES requires careful management of keys, including their distribution and storage. If keys fall into the wrong hands, it can compromise the security of the system.
- Vulnerable to Attack: While PKES is highly secure, it can still be vulnerable to attacks such as brute force attacks, man-in-the-middle attacks, and side-channel attacks.
- Implementation Issues: PKES requires careful implementation to ensure that it is secure. Poorly implemented PKES can have vulnerabilities that can be exploited by attackers.
- Dependence on Trust: PKES relies on trust between the parties involved. If one of the parties is not trustworthy, it can compromise the security of the system.
In conclusion, PKES is a highly secure and widely used encryption method. While it has its advantages, it also has its disadvantages, such as computational complexity, key management, and vulnerabilities to attacks.