Are you interested in cybersecurity? If you are, then you’ve probably heard of ChipWhisperer. It’s an open-source toolchain that allows researchers and engineers to perform side-channel analysis (SCA) and fault injection attacks on embedded devices. But what exactly is the ChipWhisperer toolchain, and why is it so attractive to cybersecurity professionals?
First, let’s start with the basics. Side-channel analysis (SCA) is a method of attacking cryptographic implementations by exploiting the physical side-effects of their operation, such as power consumption, electromagnetic radiation, and timing variations. These side-effects can reveal information about the cryptographic key being used, allowing an attacker to recover it without having to break the encryption directly.
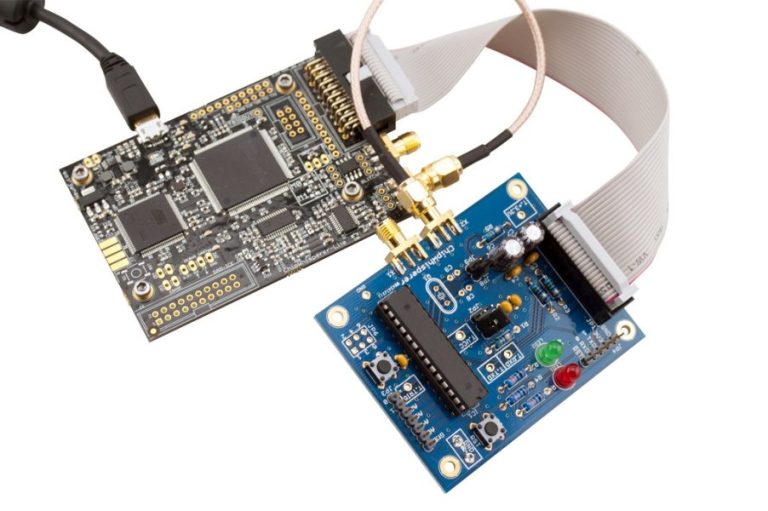
Now, enter the ChipWhisperer toolchain. It’s an integrated set of tools that can help you perform SCA on embedded devices. The ChipWhisperer toolchain includes hardware (such as a target board and a capture board), software (such as Python-based scripts and Jupyter notebooks), and documentation. With this toolchain, you can perform power analysis, electromagnetic analysis, glitching, and other SCA techniques.
One of the key advantages of the ChipWhisperer toolchain is its open-source nature. This means that anyone can access and modify the source code, making it more transparent and trustworthy. Additionally, because the toolchain is open-source, it’s constantly being updated and improved by a community of developers and researchers. This means that the toolchain is always up-to-date with the latest techniques and advancements in the field.
Another advantage of the ChipWhisperer toolchain is its ease of use. Even if you don’t have a lot of experience with SCA, the toolchain comes with detailed documentation and tutorials that can help you get started. Additionally, the toolchain is designed to be modular, meaning that you can choose which components to use depending on your specific needs.
But perhaps the most attractive feature of the ChipWhisperer toolchain is its versatility. Because it supports a wide range of SCA techniques, you can use it to attack a variety of embedded devices, from simple microcontrollers to more complex systems-on-chip. This makes it an essential tool for anyone interested in the security of embedded systems.
In conclusion, the ChipWhisperer toolchain is an open-source, easy-to-use, and versatile toolset for performing side-channel analysis and fault injection attacks on embedded devices. Whether you’re a cybersecurity professional or just interested in the field, the ChipWhisperer toolchain is a must-have tool in your arsenal. With its constantly evolving features, and active community of developers, the ChipWhisperer toolchain is a powerful tool for anyone looking to analyze the security of embedded systems.
One of the key components of the toolchain is the capture board, which is used to measure and record the side-channel signals generated by the target device. The capture board connects to the target device through a JTAG or SWD interface and uses high-speed ADCs to capture the relevant signals. The captured data is then sent to a host computer for analysis.
On the software side, the ChipWhisperer toolchain provides a Python-based interface for controlling the capture board and analyzing the captured data. The interface includes a variety of tools for performing different types of attacks, such as power analysis, electromagnetic analysis, glitching, and more. The toolchain also includes Jupyter notebooks, which provide a user-friendly interface for working with the captured data and running analysis scripts.
One of the strengths of the ChipWhisperer toolchain is its modular design. The toolchain is composed of a number of different components that can be combined and customized depending on the specific needs of the user. For example, you can choose different capture boards depending on the target device and the type of attack you want to perform. Similarly, you can select different analysis tools depending on the type of side-channel signal you want to work with.
Another benefit of the ChipWhisperer toolchain is its active community of developers and users. The toolchain is open-source, which means that anyone can contribute to its development and share their own analysis scripts and techniques. The ChipWhisperer community is also very active on forums and social media, providing support and sharing their own experiences with the toolchain.
Overall, the ChipWhisperer toolchain is a powerful and flexible set of tools for performing side-channel analysis and fault injection attacks on embedded devices. Its open-source nature, ease of use, and versatility make it an attractive choice for anyone interested in the security of embedded systems. Whether you’re a cybersecurity professional, a hardware engineer, or just someone interested in exploring the field of SCA, the ChipWhisperer toolchain is a valuable resource to have at your disposal.
Advantages:
- Open-source: The ChipWhisperer toolchain is open-source, meaning that its source code is freely available to everyone. This makes the toolchain more transparent and trustworthy, as anyone can review and modify the code as needed.
- Versatility: The ChipWhisperer toolchain supports a wide range of side-channel analysis and fault injection techniques, making it a versatile tool for attacking different types of embedded devices.
- Ease of use: The ChipWhisperer toolchain comes with detailed documentation and tutorials, making it easy for even beginners to get started with side-channel analysis.
- Active community: The ChipWhisperer toolchain has an active community of developers and users, who contribute to the development of the toolchain, share analysis scripts and techniques, and provide support for other users.
- Modularity: The ChipWhisperer toolchain is designed to be modular, allowing users to choose which components to use based on their specific needs.
Disadvantages:
- Limited hardware support: While the ChipWhisperer toolchain supports a wide range of side-channel analysis and fault injection techniques, its hardware support is more limited. This means that the toolchain may not be compatible with all types of embedded devices.
- Cost: The hardware components of the ChipWhisperer toolchain, such as the capture board, can be expensive, which may be a barrier to entry for some users.
- Steep learning curve: While the ChipWhisperer toolchain comes with documentation and tutorials, the process of performing side-channel analysis can still be complex and require a steep learning curve.
- Legal issues: The use of side-channel analysis and fault injection attacks on embedded devices may be illegal in some jurisdictions, which could limit the use of the ChipWhisperer toolchain in certain contexts.
- Limited scope: While the ChipWhisperer toolchain is a powerful tool for attacking embedded devices, it is not a silver bullet solution for all security challenges. It is important to consider other security measures, such as encryption and authentication, in addition to side-channel analysis.