Search
-
C / Cryptography / Programming / YouTube
Shannon’s Entropy: Detecting Encryption and Compression in Data
December 31, 2024
-
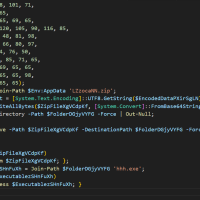
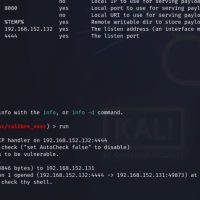
Analyzing Phishing Attacks: Lumma Stealer and PowerShell Obfuscation
December 30, 2024
-
C / Cryptography / Programming / YouTube
Shannon’s Entropy: Detecting Encryption and Compression in Data
December 31, 2024
-
Analyzing Phishing Attacks: Lumma Stealer and PowerShell Obfuscation
December 30, 2024
-
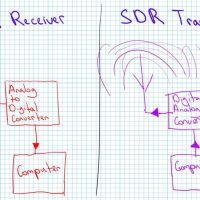
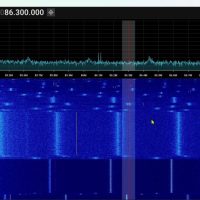
A Beginner’s Guide to Navigating SDR++: Mastering the Basics
December 16, 2024
- Android Can Bus CAN Bus Module Can Protocol Paket Layout car Car ECU Car Immobiliser Car Repair Car Tuning Car wiring Chip Tuning Computer Forensics Cyber Security Digital Forensics DSRC ECU Map Reading ECU Map Training ECU Reflashing ECU VE EEPROM EPROM Error ethical Hacking Fix Forensics Java Kotlin MAC Address Metasploit OBD-İİ Programming Reverse Engineering Software Defined Radio Stage 1 Stage 2 Stage 3 Standalone ECU What are they used for What EMS Means ? What is Can bus What is Cyber security What is DSRC What is Standalone ECU Windows Forensics YouTube